Please note that this post assumes you have a basic understanding of the tools mentioned or are willing to conduct your own research. It will not cover detailed explanations of each tool.
Managing SSL certificates can be a challenging task when renting a server and attempting to set up a website with a custom domain. While there are several services available to assist, they may require the use of their services or additional fees.
Good news is there are already ton of tools that can do the job.
Introduce Let’s Encrypt
Let’s Encrypt is a non-profit CA that provides free SSL/TLS certificates to enable website owners to encrypt their website traffic and enhance their website’s security. It was launched in 2015 with the goal of making HTTPS encryption ubiquitous on the web, and it has since become a widely used CA due to its free and automated certificate issuance process.
To enable HTTPS on your website, you need to get a certificate (a type of file) from a Certificate Authority (CA). Let’s Encrypt is a CA. In order to get a certificate for your website’s domain from Let’s Encrypt, you have to demonstrate control over the domain. With Let’s Encrypt, you do this using software that uses the ACME protocol which typically runs on your web host.
From Let’s Encrypt
We recommend that most people with shell access use the Certbot ACME client. It can automate certificate issuance and installation with no downtime. It also has expert modes for people who don’t want autoconfiguration. It’s easy to use, works on many operating systems, and has great documentation. Visit the Certbot site to get customized instructions for your operating system and web server.
What’s Certbot?
You can see another noun, Certbot, in the previous paragraph. Certbot is one of the recommended tools to obtain and install SSL/TLS certificates from Let’s Encrypt, and it automates the process of certificate issuance and renewal, making it easier for website owners to keep their sites secure.
If you’re interested, you can review the details of how it works. However, for the purpose of this discussion, I’m going to skip ahead to the next step.
What’s Docker?
Docker is an open-source platform that enables software developers to build, package, and deploy applications in lightweight, portable containers. Containers allow developers to isolate and run their applications and their dependencies in a self-contained environment, ensuring that the application runs consistently across different computing environments.
What’s Nginx?
Nginx is a free and open-source web server software that can handle a large number of connections and requests. It’s known for its high performance, reliability, and scalability, making it a popular choice for high-traffic websites and applications. It can be used as a front-end web server, load balancer, or proxy server, and is highly customizable with a variety of third-party modules and plugins available.
By setting up virtual hosts or server blocks, you can define different server configurations for each subdomain. Each server block can have its own root directory, SSL certificate, proxy settings, and more. Nginx will then route incoming requests based on the specified server name (subdomain) in the HTTP headers.
What we are going to do?
We will be leveraging these tools to assist us in completing the task, or more specifically, we will be tapping into the power of the open-source community, where someone has already created a Docker image to simplify the process for us.
https://github.com/JonasAlfredsson/docker-nginx-certbot
You can go through README and Good to know first.
Let’s get it started
Make sure that you have installed Docker and Docker Compose.
How to install Docker, you can check here.
How to install Docker Compose, you can check here.
I prefer Docker Compose over standalone Docker because it enables me to conveniently configure all the necessary components in a single file, eliminating the need for multiple commands.
Here is the docker-compose file I have been using for a while
version: '3'
services:
nginx:
image: jonasal/nginx-certbot:latest
restart: unless-stopped
env_file:
- ./nginx-certbot.env
ports:
- 80:80
- 443:443
volumes:
- ./nginx_secrets:/etc/letsencrypt
- ./user_conf.d:/etc/nginx/user_conf.d
- ./html:/usr/share/nginx/html
extra_hosts:
- "host.docker.internal:host-gateway"
networks:
default:
external:
name: service-networkWe can just pull jonasal/nginx-certbot image directly and set it up via docker-compose.
env_file: nginx-certbot service will load environment variables from the nginx-certbot.env file. Details please check out here. The service will create and renew the SSL certificate based on this setting.
# nginx-cerbot.env example
# Required
CERTBOT_EMAIL={your.email}
# Optional (Defaults)
DHPARAM_SIZE=2048
ELLIPTIC_CURVE=secp256r1
RENEWAL_INTERVAL=8d
RSA_KEY_SIZE=2048
STAGING=0
USE_ECDSA=1
# Advanced (Defaults)
CERTBOT_AUTHENTICATOR=webroot
CERTBOT_DNS_PROPAGATION_SECONDS=""
DEBUG=0
USE_LOCAL_CA=0
volumes: Several directories are being mounted as volumes, including ./nginx_secrets for Let’s Encrypt certificates, ./user_conf.d for custom Nginx configurations, and ./html for serving HTML content.
extra_hosts: setting allows the Nginx container to access services running locally on the host machine.
Since I’m not an expert in Nginx configuration, I would recommend seeking additional resources on the internet to obtain more accurate and detailed information about Nginx configuration files.
Here, I will just provide some configuration files that I’m using and it works.
Regarding the Nginx confuration for WordPress, I reference the post here.
# WordPress configuration example
upstream wordpress_site {
server wordpress_site:80;
}
server {
listen 443 ssl;
server_name {your.domain.com};
# Load the certificate files.
ssl_certificate /etc/letsencrypt/live/{your-domain-com}/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/{your-domain-com}/privkey.pem;
ssl_trusted_certificate /etc/letsencrypt/live/{your-domain-com}/chain.pem;
# Load the Diffie-Hellman parameter.
ssl_dhparam /etc/letsencrypt/dhparams/dhparam.pem;
location / {
try_files $uri @apache;
}
location ~ ^/.user.ini {
deny all;
}
location ~* .(svg|svgz)$ {
types {}
default_type image/svg+xml;
}
location = /favicon.ico {
log_not_found off;
access_log off;
}
location = /robots.txt {
allow all;
log_not_found off;
access_log off;
}
location @apache {
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Host $host;
proxy_pass http://wordpress_site;
}
location ~[^?]*/$ {
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Host $host;
proxy_pass http://wordpress_site;
}
location ~ .php$ {
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Host $host;
proxy_pass http://wordpress_site;
}
}
If you have a static website, for example, your portfolio. You can just put your static web files in ./html and add a Nginx configuration like this.
# static website configuration
server {
listen 443 ssl;
server_name {your.domain.com} {your.second.domain.com};
# Load the certificate files.
ssl_certificate /etc/letsencrypt/live/{your-domain-com}/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/{your-domain-com}/privkey.pem;
ssl_trusted_certificate /etc/letsencrypt/live/{your-domain-com}/chain.pem;
# Load the Diffie-Hellman parameter.
ssl_dhparam /etc/letsencrypt/dhparams/dhparam.pem;
location / {
# If you put it in a sub-folder under /html, then you can adjust the root path accordingly.
root /usr/share/nginx/html;
try_files $uri /index.html;
}
}If you did setup extra_hosts, by adding the IP address 172.17.0.1 or host.docker.internal followed by the specific port, the Nginx docker instance can establish communication with the corresponding local service. For example, if a service is running on port 8080 locally, the Nginx container can access it using the URL http://172.17.0.1:8080 or http://host.docker.internal:8080.
Domain and sub-domain management
It’s quite simple. You can just go to your domain provider website. For me, I choose Google Domain, so I log into my Google account and go to Google Domain then select DNS section.
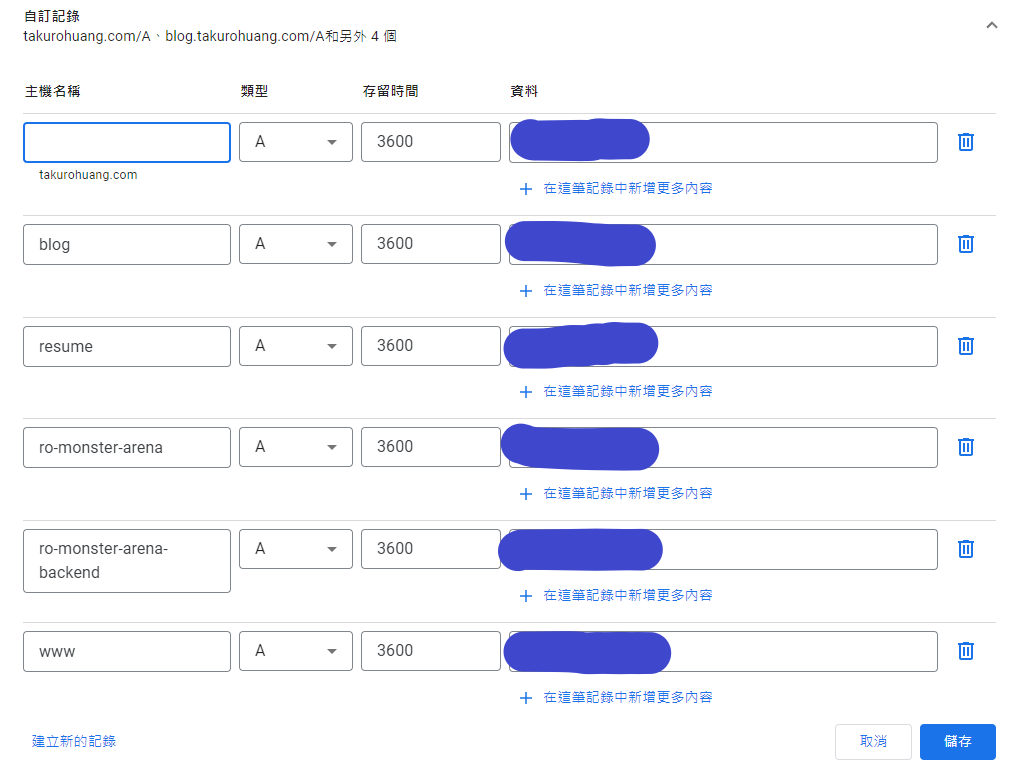
To add records for your subdomain, you typically need to access the DNS management interface provided by your domain registrar or DNS hosting provider. Within this interface, you can create new DNS records, specifying the subdomain name and the corresponding server IP address.
Once the DNS records are updated, it may take some time for the changes to propagate across the internet. This propagation process, known as DNS propagation, can take anywhere from a few minutes to several hours, depending on various factors such as TTL (Time to Live) settings and caching by DNS resolvers.
Hope this helps!
Reference:

搶先發佈留言